What better way to beat your competition than to know what they are working on and then steal it? What am I talking about? Corporate espionage. Corporate Espionage and Data BreachesCorporate espionage takes many forms, but what we are seeing recently is a tremendous amount of businesses sending in – for lack of better words – spies to their competition and...
Read MoreSince we became a Cloudflare partner, we’ve been asked multiple times: What is a DDoS?The Rundown on DDoS AttacksA DDoS is a distributed denial of service attack.Years ago when a business needed to get online, they purchased web hosting services through many web hosting companies. It was usually on a single server for the client, shared between multiple other clients...
Read MoreWhy do we recommend a VPN when you have nothing to hide? With the end of net neutrality, ISPs and Internet providers have now free reign to do as they please with on how you receive your data. We’ve already seen it with our commercial clients on how to access their services. A Matter of Priority A prime example is prioritization of the...
Read MoreNot Even Once.In the last couple months a wireless vulnerability known as KRACK (Key Reinstallation Attack) was discovered. Basically, this exploit takes advantage of how the devices hand off each other’s encryption keys. Most major brands of wireless providers such as like one we use called Ubiquiti were patched within hours if not days. But most of the small businesses...
Read MoreAt Triton Technologies, security is in the forefront of our mind on every level. That includes stuff and technologies that we do not have direct access to or complements our client's networks. One of those such complementary services is web hosting and web page public facing servers.The Rise of Denial of Service Attack ServicesOver the last couple months, we noticed...
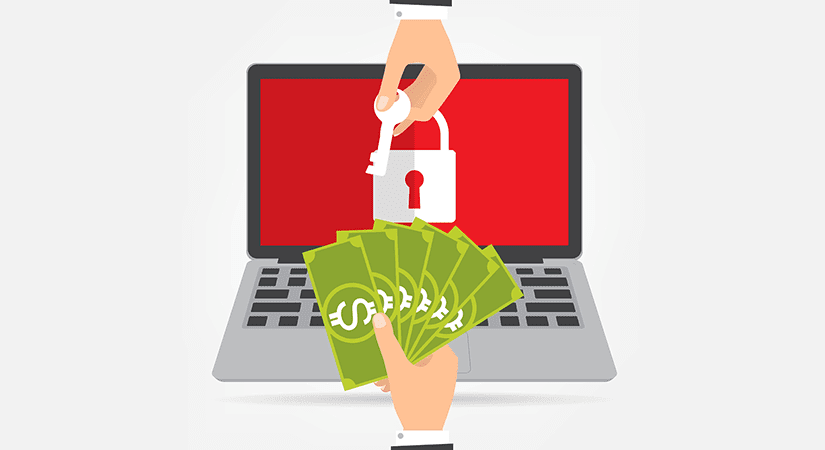
Read MoreOn Dealing With Ransomware A couple of weeks ago, a worldwide exploit stolen utilities from the National Security Agency were utilized to take down literally hundreds of thousands of computers, from hospitals, government, and large corporations. For days people were freaking out and having a tremendous time securing their networks. Traditional methodologies failed. Traditional thought processes failed. In the days and weeks since...
Read MoreOver a month ago, Triton Technologies was given a challenge. The challenge was simple: break our wireless network and you have our security contract. Sounds great in theory, but in reality white hat hacking is a quite complex method and time-consuming. Security Penetration: Break Their Wireless Network We had been trying to acquire this company for years and we knew their shortcomings, insecurity...
Read MoreWe have received a lot of requests for this and it’s a scorcher. “How do I protect my corporate privacy this day in age?”Let’s Get Right to the Answer: You Can’tAt least not easily. What do we mean? Quite simply this, every company in every country cooperates with the government of that country. From China, to France, UK, Russia and...
Read MorePlease, please stop.In marketing, it is great to give your business a personal face: a close contact or a person to call when things go wrong. That is great, but it causes a tremendous security headache in I.T. when you paint that target.What are we talking about? A common scam known as phishing. Phishing Targeting You and Your StaffThe way...
Read More