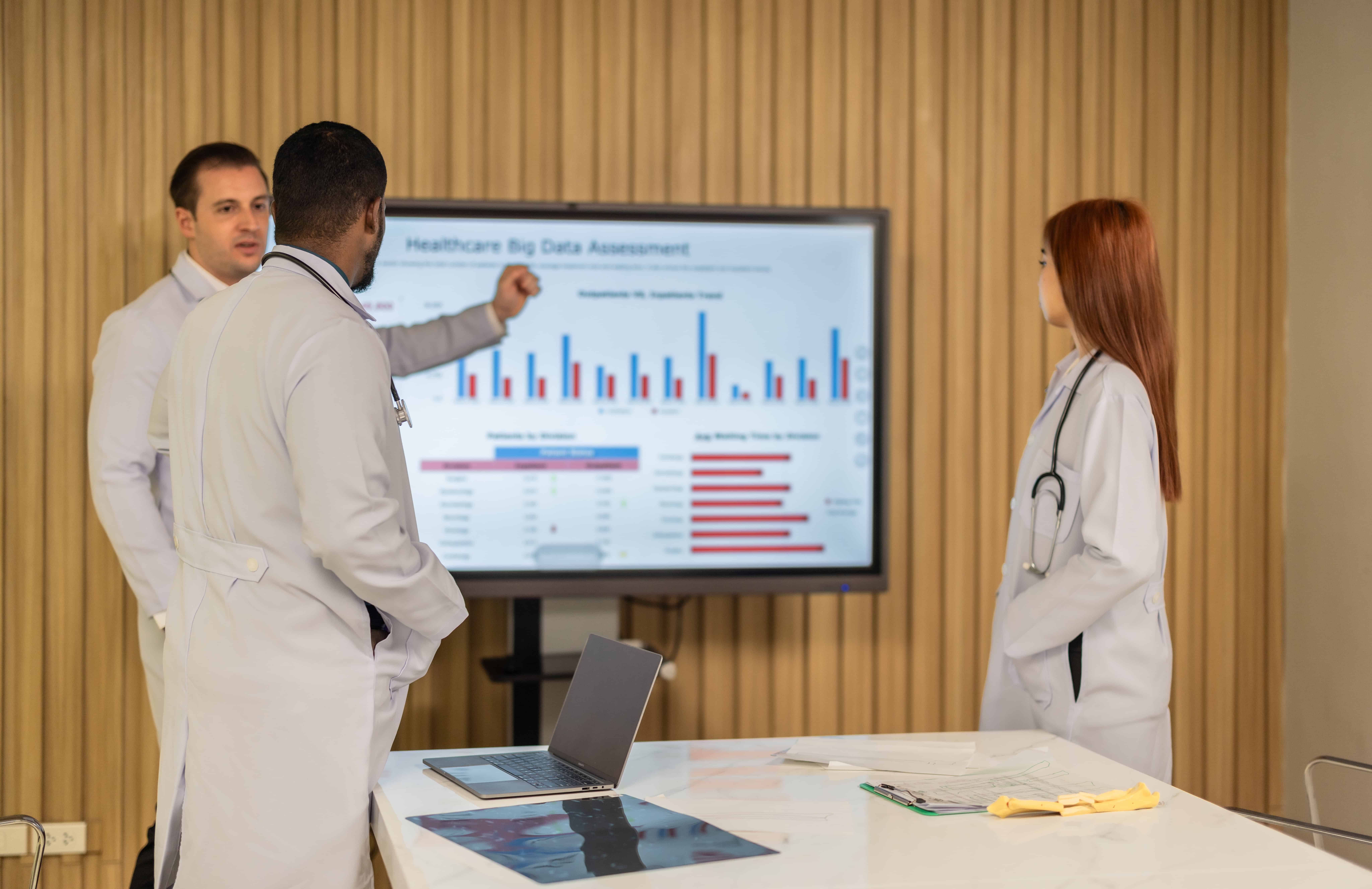
Healthcare breaches have emerged as a pressing concern in recent years, escalating in frequency and severity across the globe. These incidents represent more than just data compromises; they signify profound threats to patient privacy, operational integrity, and the trust that underpins the healthcare provider-patient relationship. The sensitive nature of the information at stake—ranging from medical histories and treatment plans to...
Read More
- Home
- About Us
- Service Locations
- Blogs
- Managed IT Services
- Managed Backup and Disaster Recovery Services
- Co-Managed IT
- Managed Cybersecurity
- Managed Hardware as a Service (HaaS)
- Managed Hosting Solutions
- Vendor Management Systems
- Cloud Managed Services
- IT Consulting
- VoIP
- Wireless Network Solutions
- Managed IT Support
- Remote IT Support
- Managed Outsourced IT Support & Solutions
- IT Compliance
- Industries
- Contact Us