This week we had the extreme pleasure of helping a business connect up multiple buildings to a central office with...
Read More
Blogs
Knowledge, advice and opinion on IT
What’s Your Fancy? PC or Mac: Both Have IT Needs
Trave Harmon
/ July 7, 2017
One of the most controversial things that we’ve ever got from clients is: why don’t we just switch to a...
Read More
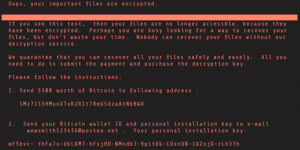
Managed IT Works: Especially Against Ransomware Like Petya
Trave Harmon
/ June 30, 2017
It’s been 6 weeks since the last global affecting ransomware attack has occurred. The last attack brought to you by...
Read More
“All-in-One” ISP Services: Too Many Cooks In The Kitchen
Trave Harmon
/ June 23, 2017
In the last decade or so we have noticed that more and more Internet service providers are offering services such...
Read More
Compliance: When You Need to See Everything from 10K Up
Trave Harmon
/ June 23, 2017
At Triton Technologies we have been doing PCI, HIPAA compliance, SOX and more for years. Most of the time it...
Read More
WannaCry or GoingtoRelax?
Trave Harmon
/ May 26, 2017
On Dealing With Ransomware A couple of weeks ago, a worldwide exploit stolen utilities from the National Security Agency were...
Read More
White Hat Hacking: Doing Wrong to Do Right
Trave Harmon
/ May 2, 2017
Over a month ago, Triton Technologies was given a challenge. The challenge was simple: break our wireless network and you...
Read More
Corporate Privacy In Today’s Environment
Trave Harmon
/ April 25, 2017
We have received a lot of requests for this and it’s a scorcher. “How do I protect my corporate privacy...
Read More
Phishing: STOP Posting Your Personnel’s Contact Information!
Trave Harmon
/ April 14, 2017
Please, please stop.In marketing, it is great to give your business a personal face: a close contact or a person...
Read More
Q&A with IT: We Love Questions
Trave Harmon
/ March 17, 2017
This week we got a new client, and it was a fantastic first meeting that it must be shared. It...
Read More
Always Online: Industries That Never Sleep
Trave Harmon
/ March 10, 2017
We have a client who absolutely must be online, ALL THE TIME. Are they a stock broker? A police station?...
Read More
Network Security: First, Middle and Last
Trave Harmon
/ March 3, 2017
We had the fun privilege this week of doing a security check for a restaurant. We have agreements with banks,...
Read More
The Importance of Thorough Vendor Evaluations
Trave Harmon
/ January 23, 2017
In the last decade, we have seen something that is somewhat upsetting. Vendor network evaluations are not worth anything. Yup, we...
Read More
Why Restaurants Need WiFi
Trave Harmon
/ November 1, 2016
If your restaurant wants to survive, it needs wifi.When it comes to selling more restaurants need to attract more clients...
Read More
Dealing with CryptoLocker: Why We Do What We Do
Trave Harmon
/ October 27, 2016
Why We Fight CryptoLocker: Our Strategy Explained As the owner of Triton Technologies, I go through constant training when it comes...
Read More
Security Risk: Why We Don’t Show Client Testimonials
Trave Harmon
/ October 21, 2016
No testimonials please.If you have been around this website for any period of time, you’ll notice no testimonials. Why?Testimonials are...
Read More
IT Hardware: Why Name Brands Make a Difference
Trave Harmon
/ October 14, 2016
The Value of Name Brands in IT Hardware Or "Why We Don’t Build Our Own IT Hardware".I know I am treading...
Read More
Taming The VoIP Beast
Trave Harmon
/ October 5, 2016
Triton Technologies years ago was created to help the business user and the business owner: over the years we have...
Read More
Why We Don’t Outsource Our Technical Support
Trave Harmon
/ September 30, 2016
The Benefits of In-House Expertise: Enhancing Customer Experience through Local Technical Support For years, as Triton Technologies grew we were...
Read More
Amazon AWS: Amazon, Part Deux
Trave Harmon
/ September 21, 2016
We get a call on Monday morning, like you do, but this one was more panic. The owner went on...
Read More