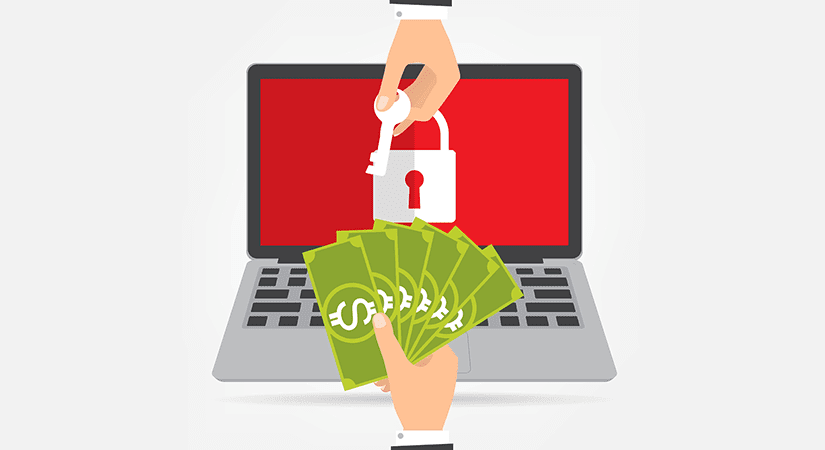
When it comes to ransomware, this cyberattack scheme isn't new, but it has become increasingly common over the past several years. Many of the viruses lurking out there steal data to be used for nefarious purposes, with the goal having long been to access important financial and personal data that can be sold off. Not ransomware. Ransomware generally does not...
Read More- Resources
- Services
- Compliance
- Industries
- About
- Contact Us