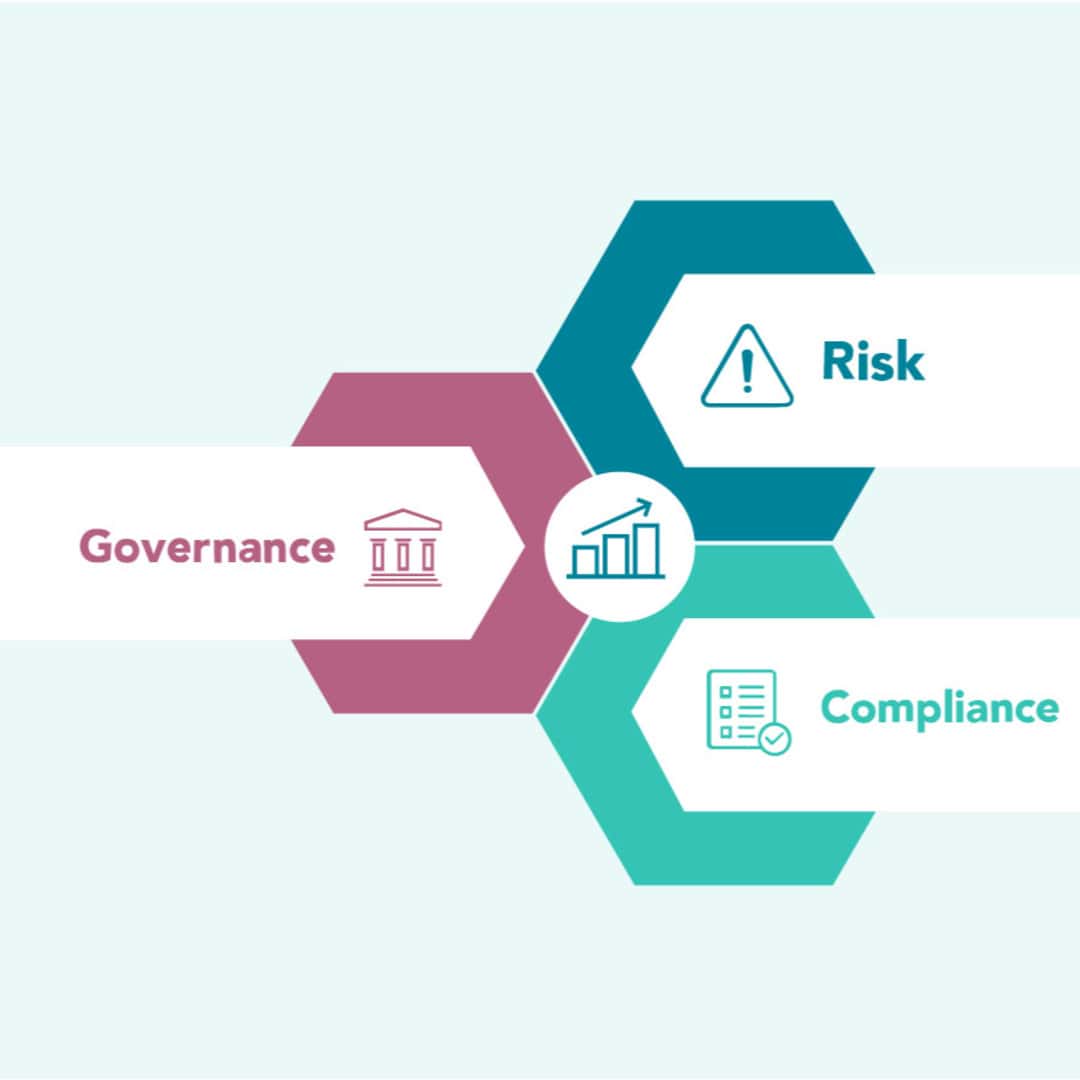
Cybersecurity Imperatives for Water Utilities: Strengthening Our Shield Amid rising concerns over the safety and resilience of the United States' critical infrastructure, the White House, alongside the Environmental Protection Agency (EPA) and the Cybersecurity and Infrastructure Security Agency (CISA), has issued stern warnings to water suppliers about the mounting cyber threats targeting the nation's water systems. These advisories highlight a growing...
Read More- Resources
- Services
- Compliance
- Industries
- About
- Contact Us